- Products
- Use Cases
- Process contractors and validate credentials
- Improve facility compliance to industry standards
- Improve speed of visitor check-in process
- Screen visitors or restrict access to my facility
- Automate my reception experience
- Improve and automate my facility evacuation process
- Manage facility security across multiple locations
- Industries
- Pricing
- Resources
- Company
Multi-Location Visitor Management & Sign-In Software
Manage Facility Security Across Multiple Entry Points
Managing compliance and security at multiple entry points - whether at one facility or spread across hundreds of locations around the world - requires a centralized solution that scales with your organization.

Easy, turnkey multi-site implementation
At iLobby, we built our business to scale with yours. All of our licenses include all hardware and software required to get up and running quickly. Our white-glove service ships each pre-configured kiosk direct to each facility or location for quick and easy implementation.

One global dashboard to manage all entry points
Manage security and compliance across multiple entry points on one platform to eliminate the confusion of spreading data across multiple solutions or siloed tools. Centralized real-time dashboards leverage data from all iLobby kiosks to streamline multiple entry point monitoring.

Custom, site-specific configurations
Compliance and security requirements for facility or visitor management systems vary between states, countries and industries. The iLobby platform is fully configurable to meet your unique needs - such as different workflows, documentation requirements, screening questions, or language options.
Learn More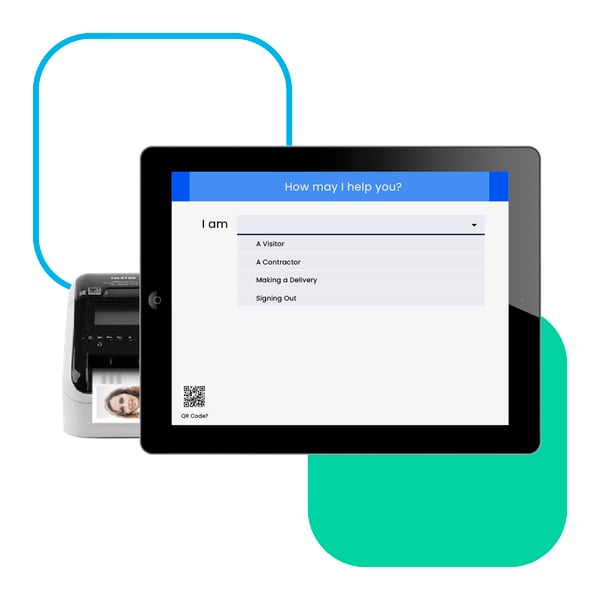
Robust role-based back-end administrative flexibility
iLobby’s platform is built with strong security and role-based permissions. Set custom permissions and user types for seamless access and to secure sensitive data. Provide global admins with permission to view the entire business at a glance from one dashboard, or restrict access to specific locations or data sets.
Our Partners Can Feel The Difference

The efficient way to manage our reception.
“The system was easier than I thought it would be to set up. From candidates arriving for interviews to customers arriving for meetings, we are able to give attention to those taking their time to give us theirs.”
Lore Balde
Administrative Assistant

It was very collaborative right from the get-go.
“It was a pleasure to deal with the people that you had on your team, the results were what we expected and there’s the capability of continuing improvement, and always good support. ”
Jeff Thorn
Manager Security Operational Support

A perfect ally in our security for access control.
“We are convinced that choosing iLobby among the existing options within the competitive market is the best decision we have taken, mostly related to security and the convenience for registering our visitors.”
Fernando Romero
Oficial de Protección de la Instalación Portuaria

The Enterprise Facility & Visitor Management Platform
iLobby's FacilityOS is a facility and visitor management platform used by security professionals, facility managers, compliance teams, and operational leadership to drive safety, security and compliance. Deployed at more than 6,000 sites worldwide, FacilityOS automates key facility process to achieve regulatory compliance, enforce safety protocols, and drive site security requirements.












