- Products
- Use Cases
- Process contractors and validate credentials
- Improve facility compliance to industry standards
- Improve speed of visitor check-in process
- Screen visitors or restrict access to my facility
- Automate my reception experience
- Improve and automate my facility evacuation process
- Manage facility security across multiple locations
- Industries
- Pricing
- Resources
- Company
Strengthening the Three Levels of Physical Security
June 13, 2023
What are the levels of physical security?
Physical security is defined as the measures taken to protect property, assets, and buildings against intruders. FacilityOS increases security by combining the core functions of facility and visitor management into one integrated system, linking sign-in kiosks and an online dashboard. This enables a single user to manage various entrances and locations remotely.
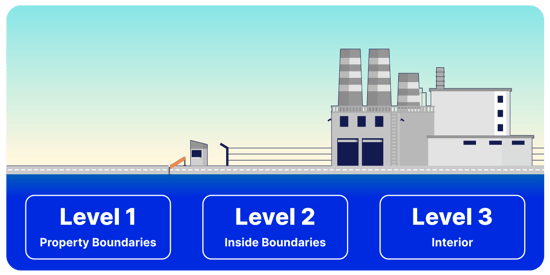
Integrating physical security software for a facility requires various levels of protection:
- Level 1- Property Boundaries
- Level 2- Inside Boundaries
- Level 3- Interior
An efficient physical security software implements at least two forms of security at every level.
Level 1 - Property Boundaries
Property boundaries are the first line of defense for physical security. When securing this perimeter, the aim is to control the bodies that drive or walk onto the grounds. Some security features in this level can include locked gates, secured by guards, or remotely operated. A hedge can offer ample perimeter security in a low-security facility, although options ramp up with security requirements.

Clients need to determine the form of perimeter security to install by assessing the risks of encroachment onto the facility against the expenses of physical security measures. The outer perimeter will include access control integration. At the same time, FacilityOS integrates with new or existing access controls for gates, turnstiles, and doors to better control the people that make it on your premises. When combined with our Physical Identity & Access Management software, credential provision can be automated with policy-based workflows.
The facility management software enables security teams to monitor sign-ins constantly. The security teams can also admit or deny entry to sensitive locations remotely via the online visitor management dashboard.
Physical security is much more than access control integration and physical security software. It can also include natural access control, using landscaping and building features to direct people exiting and entering the property. In theory, a criminal's perceived risk when visiting your property is reduced if they believe they can move unnoticed.
Furthermore, it is integral to add territorial reinforcements as it helps distinguish public spaces from private spaces or property, preventing unauthorized entry. It is imperative to enable authorized personnel with a sense of authority. Authorized security personnel can detect visitors that seem out of place, as the environment makes it difficult for intruders to blend in.
Level 2 - Inside Boundaries
This level of physical security secures a facility’s walls, windows, and doors. Typically, alarm systems are used to protect this perimeter using a warning alarm if an exit or entry is breached. Nevertheless, it is pertinent to note that not every potential threat entering the facility will activate an alarm. The Inner Perimeter may require security such as access control integration, keys, locks, key controls, and electronic visitor management software.

All of these measures play a role in ensuring unauthorized personnel are kept out of the building. These components also ensure that the flow of visitors to the building is controlled. To achieve this, facility management software leverages watchlists, monitoring visitors via sign-in kiosks. These sign-in kiosks are integrated with custom and government watchlists. The visitor management software screens visitors against pre-set watchlists to identify potential threats. The implemented physical security software automatically notifies security when potential threats are identified while denying entry to said individuals.
Level 3 - Interior
This third level makes up the levels of physical security. By definition, interior security addresses the facility's interior, where data stores, employee offices, and other pertinent assets are housed. Motion detectors and security cameras can be quite effective at monitoring the interior space of any building.
These components are further bolstered by electronic access control systems—with ID scanning and document collection features—all of which control traffic flow within a building and stop unauthorized persons at the door.

A visitor management system is placed, preferably in a central lobby, scans Identification, saves identification information, and records visit times on each person requesting access to the building. Furthermore, automation allows for instant background checks on visitors, alerting security and creating logs of attempted check-ins and denials.
Conclusion
The three levels of physical security all play an important role in providing overall security for a facility. Multi-location visitor management, access controls, ID scanning, Watchlists, and more all work together to create an air-tight and secured facility.
iLobby encourages a proactive, tech-driven, and comprehensive approach to security, as this approach effectively keeps people safe.
Matthew Kieswetter
Matthew is a Senior Sales Manager at iLobby, valued for his expertise in building and leading robust sales teams. Passionate about the outdoors and basketball, he brings the same dedication to fostering iLobby’s sales team's growth as he does to his personal pursuits.
Related Posts
View All Posts
Visitor Management
9 min read
How Automated Visitor Management Works & 8 Critical Processes to Automate
Continue Reading
Visitor Management
4 min read
How Including Safety Training in Your Visitor Check-In Process Saves Time
Continue Reading
Emergency Management
5 min read

